The message you see here hit one mother right between the eyes when she picked up her kids at a day care center outside Houston. She posted her reaction on Facebook to this sign, and it generated nearly 1.5 million shares. I say it’s a wake-up call to a disturbing trend.
Too many people just don’t know when to put their phones in their pockets – or close their connected devices. I find it disrespectful and representative of misplaced priorities.
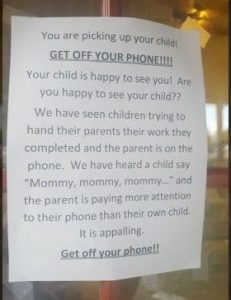
The sign read:
“You are picking up your child! GET OFF YOUR PHONE!!!! Your child is happy to see you! Are you not happy to see your child??”
“We have seen children trying to hand their parents their work they completed and the parent is on the phone. We have heard a child say ‘Mommy, mommy, mommy…” and the parent is paying more attention to their phone than their own child. It is appalling. Get off your phone!!”
The sign and reaction of the mother were the subject of a Fox News report. The mother said she usually doesn’t have her phone when she picks up her children. But this time, it was in her hand. She said she thought the message was awesome and decided to snap the picture and post it on her Facebook page.
Naturally, there was some pushback. One Facebooker commented that she would pull her child out of a daycare center that posted a message like that, and another said her work keeps her on call.
I don’t what kind of work she does, but this strikes me as a misplaced priority. I know there are emergencies: work, family, disasters, etc. But I also know there can be a time when we need to put our phones away and give proper attention to our families – especially to the children whose lives we are shaping by our words and deeds.
So, I applaud the sign and the mother who posted it. And, I want to take it a step farther to talk about phones in places where they shouldn’t be used, such as houses of worship.
I am not an especially religious person, but I attend a synagogue in my community, and I am always shocked by the number of phones that are out. Sometimes, they are out inside the sanctuary, and that’s disrespectful of those who want to worship. I also see children and adults alike using their phones in the lobbies of their houses of worship, and I wonder why they just don’t go outside.
It’s equally disrespectful for people to use their phones during movies, concerts and plays – even if they are just texting. It disrupts everyone nearby, and in some cases, it can affect performers.
Yes, I know it’s good to have a phone handy to handle real emergencies, but you can keep a phone on vibrate, and you can leave the building if your attention is required by someone. That way, you can maintain respect for people and institutions. What do you think? Leave a comment or send us an email to let us know.